Configure SSL in Tomcat
SSL configuration in Tomcat is a common task. Let’s look at both one-way and two-way SSL. In case you don’t have the tomcat installer, just use yum to download the opensource package:
yum install tomcat
Use this link to create a Java Keystore using Kytool Command. Alternatively, use my Keystore with self-signed cert.
One-Way SSL Configuration
This type of SSL indicates that the Client will validate Tomcat Server’s Certificate but the Tomcat Server does not care about what certificate (or without certificate), the client is trying to connect to. Follow below steps to configure from scratch.
- Open the server.xml under <Tomcat_Home>/conf/
- Search for the below snippet
<Connector port=”8443″
protocol=”org.apache.coyote.http11.Http11Protocol”
maxThreads=”150″
SSLEnabled=”true”
scheme=”https”
secure=”true”
clientAuth=”false”
sslProtocol=”TLS”/>
- Replace the above snippet, with below one, or add, if not present:
<Connector port=”8443″
protocol=”org.apache.coyote.http11.Http11Protocol”
maxThreads=”150″
SSLEnabled=”true”
scheme=”https”
secure=”true”
clientAuth=”false”
ciphers=”TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_GCM_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA384″
keyAlias=”middlewareworld.org”
keyPass=”P@ssw0rd”
keystoreFile=”/etc/ssl/middlewareworld.org.jks”
keystorePass=”P@ssw0rd”
keystoreType=”jks”
sslEnabledProtocols=”TLSv1.2″
truststoreFile=”/etc/ssl/middlewareworld.org.jks”
truststorePass=”P@ssw0rd”/>
Note that the ciphers specified is just an example. Update the list as per need, or company policy. Now try accessing the page using https://<IP>:8443/<your_application_context>
If using self-signed certificate, you see below error, upon clicking the certificate button in browser:
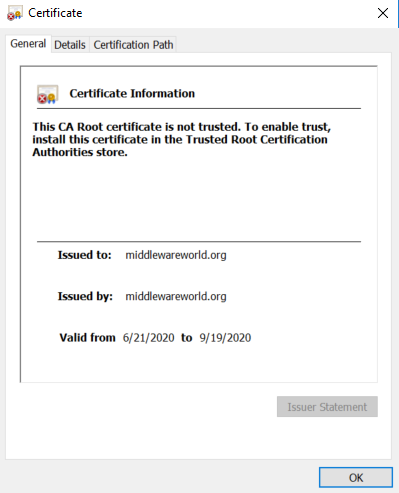
But that is perfectly alright, since the error will go away if CA signed certificates are used.
Two-Way SSL Configuration
In two-way SSL, both Tomcat Server has to trust Client Certificate, and vice versa. Hence, this is more secure. To implement, just use the same snippet as above in server.xml with only one change as highlighted:
<Connector port=”8443″
protocol=”org.apache.coyote.http11.Http11Protocol”
maxThreads=”150″
SSLEnabled=”true”
scheme=”https”
secure=”true”
clientAuth=”true”
ciphers=”TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_256_GCM_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_256_CBC_SHA384″
keyAlias=”middlewareworld.org”
keyPass=”P@ssw0rd”
keystoreFile=”/etc/ssl/middlewareworld.org.jks”
keystorePass=”P@ssw0rd”
keystoreType=”jks”
sslEnabledProtocols=”TLSv1.2″
truststoreFile=”/etc/ssl/middlewareworld.org.jks”
truststorePass=”P@ssw0rd”/>
- Restart tomcat, and test the connection using below curl command:
curl -v –cacert ./middlewareworld.org.cer –key ./middlewareworld.org.key –cert ./middlewareworld.org.cer https://<IP>:8445/index.html
Important : To invoke the URL using curl, you need to extract the cert and key from the Java Keystore (JKS), that is being used in Tomcat Server. Use below command to do that:
keytool -importkeystore -srckeystore middlewareworld.org.jks -destkeystore middlewareworld.org.p12 -deststoretype PKCS12 openssl pkcs12 -in ./middlewareworld.org.p12 -nodes -nocerts -out ./middlewareworld.org.key openssl pkcs12 -in middlewareworld.org.p12 -nodes -out middlewareworld.org.cer
Use this link for other similar commands.
Below is a screenshot demonstrating the connection from client to server from my PC. Note that browser doesn’t work for this case, since we are using self-signed certificate, and browser cannot trust that.
Hope you liked the post. Please subscribe to my blog for further updates. Feel free to comment for feedback/questions.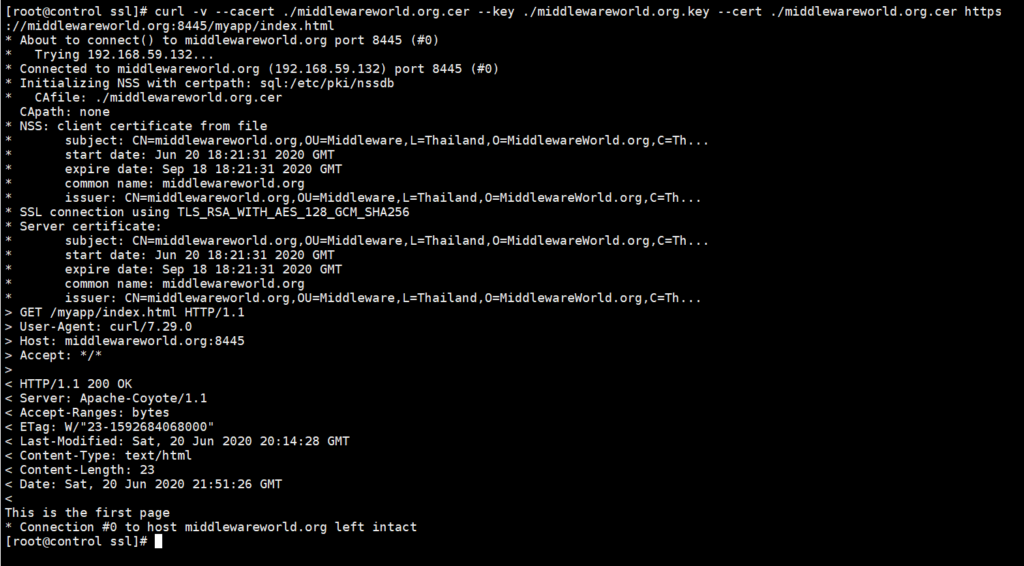
One thought on “Configure SSL in Tomcat”
Leave a Reply
Good post. Loved it.